Blind Digitial Signature Voting Scheme (Non-technical Explanation)
The Non-Technical Guide for the Average Reader and Less Tech-Savvy Cryptocurrency Enthusiast
The Problem:
Yesterday I wrote an article about my implementation of a blind digital signature voting scheme… however I got too technical. I used some scary math terms like “pick a unit of a field modulo p.” Yuck!
The Solution:
This article is in response to that article, which may be found here. The GOAL of this article is to inform the more casual reader about blind digital signatures. I will split this article into three parts:
Digital Signatures
The Zero Knowledge Proof
Blind Signatures and Voting
Digital Signatures
Nearly everyday people are asked to sign documents.
This signature is a way of verifying the authenticity of a document; it gives a person a receipt that verifies a transaction was valid or a document authorized/official.
In the 21st century, we deal with digital documents, digital receipts, digital messages, and digital transactions. How can we verify/authenticate these things in the same way we do for physical things? The answer is digital signatures. A digital signature is essentially a mathematical scheme for verifying/authenticating data. A digital signature addresses three things:
Authenticates the identity of the sender
a) Every sender will produce a unique mathematical signature
b) Thus, a signature may be tied to a user's identity so it is possible to prove I sent data to you
Forbids the sender from denying having sent the data
a) As a consequence of the first bullet point, it is possible to prove someone sent data
b) Therefore, I cannot deny that I sent data to you
Verifies the data was not tampered with
a) Signatures rely on (and are mathematically generated by) the actual data
b) Therefore if the data is tampered with, the signature will not verify
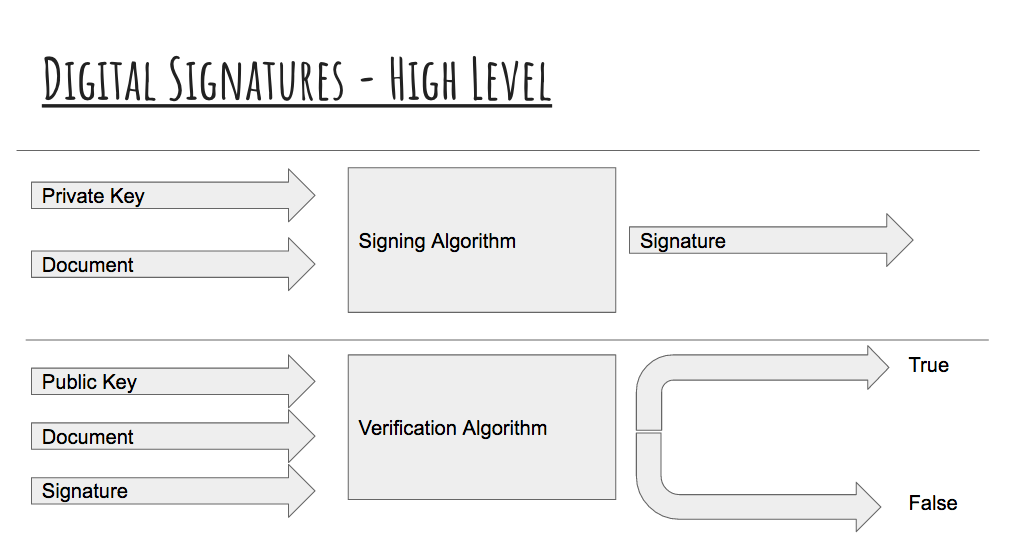
This system is based on public key cryptography. In public key cryptography, people use public keys to encrypt data and send it to the user of the public key. The user will then use their private key to decrypt the data. While everyone knows the user’s public key, they don’t know the user’s private key. Thus, only the user can decrypt messages sent to himself/herself.
Digital signatures are sort of a reverse of this system. Users sign documents using their private key and these documents are “tied” to the user’s public key; to verify a document, the verifier uses the public key of the signer, the signature, and the document.
Here is a high level diagram of the digital signature process:
The Zero Knowledge Proof
Before we jump into blind signatures, which are simply an application of digital signatures, let’s explore the idea of a zero knowledge proof. A zero knowledge proof is: a way for person A to prove to person B they know something without revealing the information they know. Here is the most classic example:
We have Alice in a purple shirt and Bob in a green shirt. Alice wants to prove to Bob that she knows the password to a secret door in a cave. Alice proposes that instead of giving the password to Bob for him to try out himself, she prove to him that she knows the password. Bob agrees and they both go to the cave. Alice proposes that if she can always appear out of the cave from the path Bob calls out, she must know the password to the door in the cave. So, she and Bob devise a plan. Alice will venture randomly down either path A or path B. Once Alice is down that path, Bob will stand at the entrance and then call out a path. If Alice knows the password to the secret door, she will be able to appear from either path no matter which path she starts down.
- Alice randomly selects either path A or path B.
- Once Alice has entered the cave, Bob enters the cave. He calls out either A or B. In this case he called out A and Alice started down path B.
- Alice, returns down the path Bob has called out. They repeat many times. If Alice knows the password, she will always be able to return down the path Bob calls out; if Bob calls the path Alice starts from, Alice must simply turn around and if Bob calls out the path Alice does not start down, Alice will simply complete the loop by opening the secret door.
Blind Signatures and Voting
In a paper by David Chaum, he outlined an application of digital signatures called blind signatures. Basically, in certain cases, people may need an authoritative figure to authenticate or verify some data, however the person may not want that authoritative figure to know the data.
The best example is a secret election. It goes like this:
Problem: A trustee wants to hold a secret election. The electors cannot meet and will have to send in their votes. However, they value privacy and want their votes to be verifiable.
Solution: Blind Signature Voting Scheme.
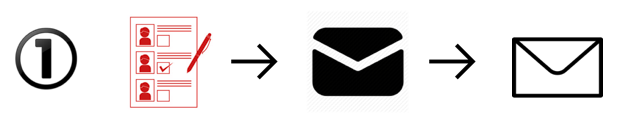
- An elector casts their ballot, puts the ballot in a carbon envelope, and puts that envelope in a plain envelope with a return address.
- The trustee receives the envelope, opens the envelope, verifies the person is eligible to vote, signs the carbon envelope, puts that envelope in a plain envelope with a return address and sends that envelope back to the elector.
- The elector receives the envelope, opens the envelope, opens the carbon envelope, verifies the signature on the ballot, puts the ballot in a plain, unmarked envelope, and sends the envelope to the trustee.
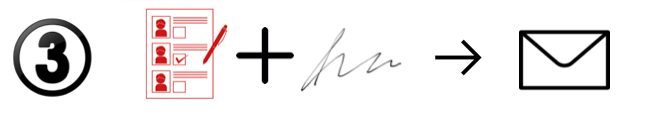
- The trustee receives the envelope, opens it, and has a verifiable ballot from an anonymous source. Part 4 image lost :(
This is the voting scheme I implemented and discussed in my last post. I hope this less technical approach makes more sense!
Conclusion
Hope this article is easier to follow @pitterpatter @steemitqa @spartanza.
If you have any questions please ask below!
To answer @spartanza:
Does this use, or can it use a digital asset residing on a Blockchain as an identifier or the representation for the digital signature?
For Bitcoin, identification is done via wallet address. Each wallet address is a series of characters that is generated from a user’s public key. Attached to this public key is a private key. Thus, the user can digitally sign transactions from their wallet with their private key. In most attacks/hacks on cryptocurrencies, people trust their private keys to third parties and these third parties are hacked. Thus, the hacker gets the private keys of wallets and can use these keys to send verifiable transactions from the hacked wallets to themselves.
Can it work with a Blockchain?
Yep! It works with Bitcoin, other cryptocurrencies, and MANY other applications (one being voting).
Bibliography:
Zero Knowledge Proof Example: http://pages.cs.wisc.edu/~mkowalcz/628.pdf
Zero Knowledge Proof Images:
- CC BY 2.5, https://commons.wikimedia.org/w/index.php?curid=313643
- CC BY 2.5, https://commons.wikimedia.org/w/index.php?curid=313645
- CC BY 2.5, https://commons.wikimedia.org/w/index.php?curid=313648
Comments